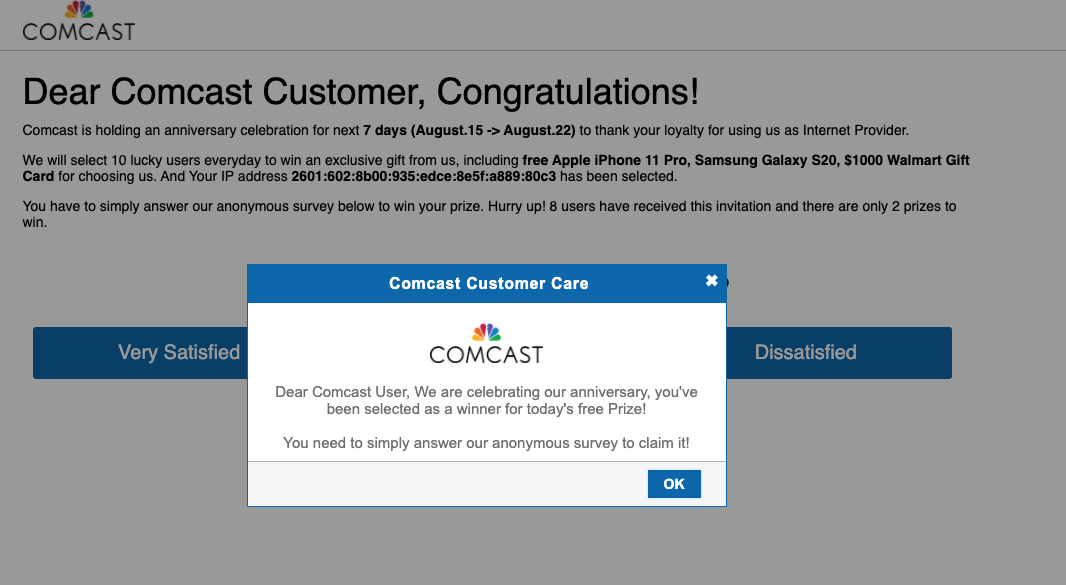
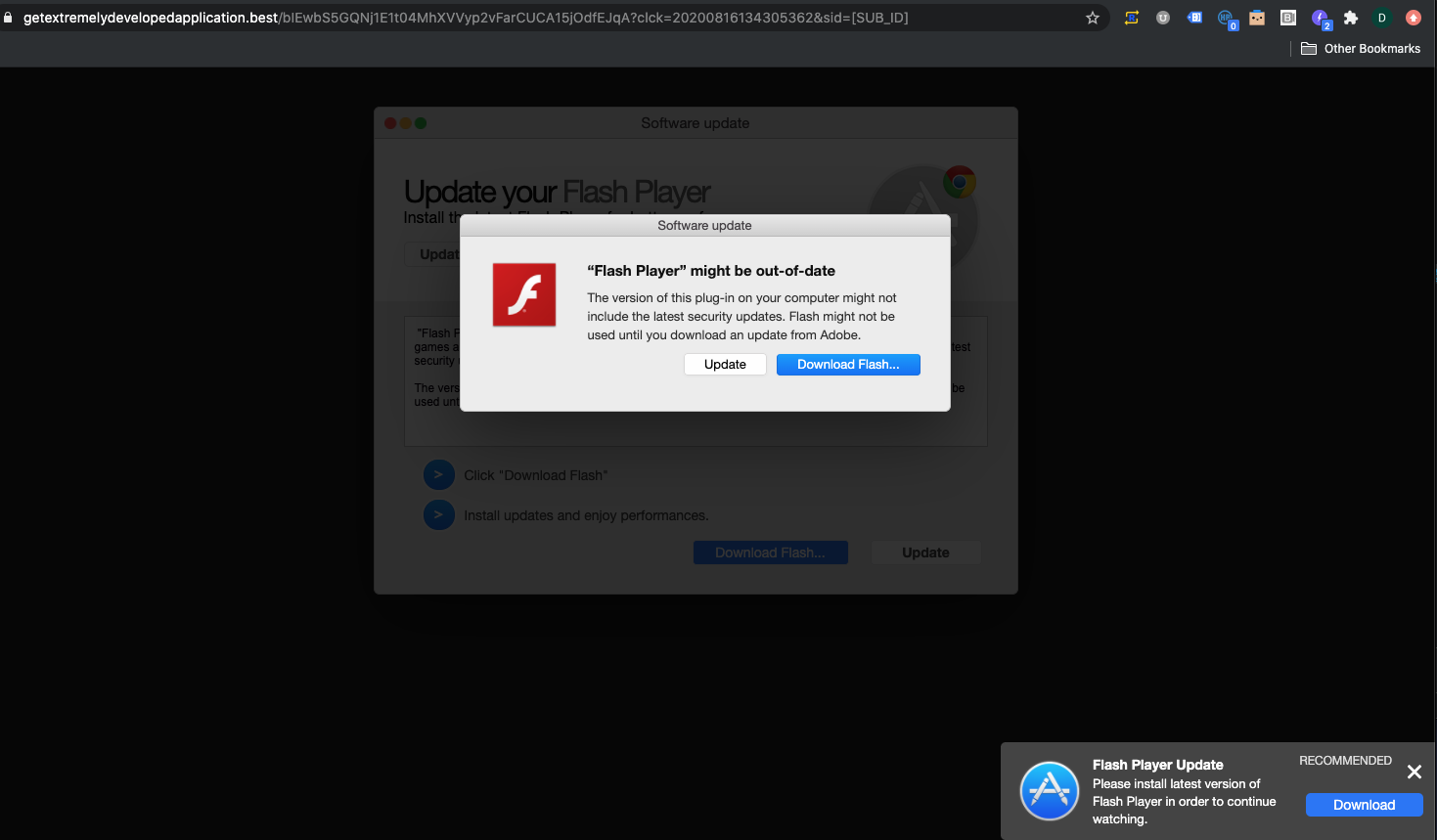
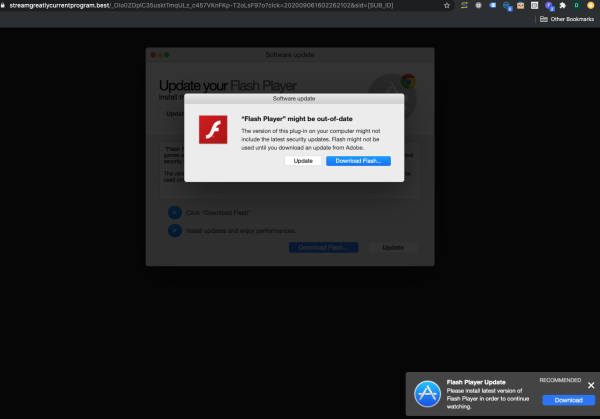
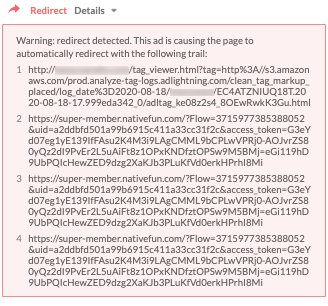
Assessment: Two widespread redirect attacks impacting 100's of publishers detected and blocked over the weekend. The campaign was primarily targeted to desktop Chrome and Safari users displaying various images based on the user's ISP connection.
One technique deployed utilized typosquatting attack techniques to redirect users to malicious scam pop-ups sites. Fraudsters create legitimate-looking URLs with minor typo errors and host their malicious code in it to carry out the redirect attack. Mostly typosquatting attacks will be unnoticed since they look nearly legitimate. One example in this attack, utilized “lijits.com” which looks nearly similar to a legitimate domain “lijit.com” an ad serving domain owned by Sovrn Holdings.
Affected platforms: Rubicon, Index, AOL/Verizon, AppNexus, TripleLift, Amobee (paused buyer already) & Celtra.
Creative and Landing Page Examples: