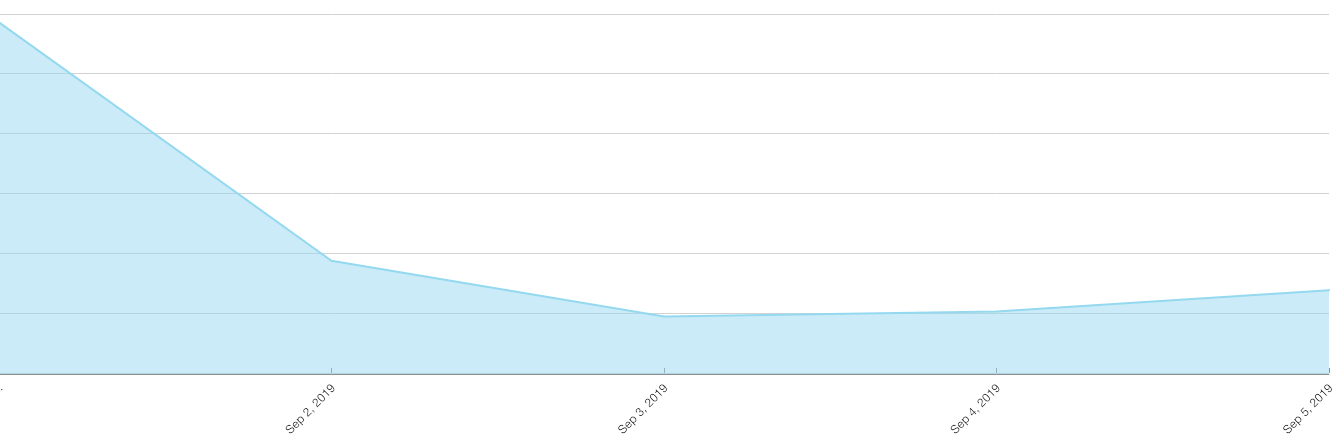
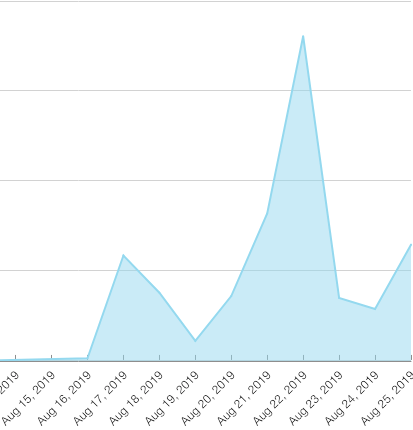
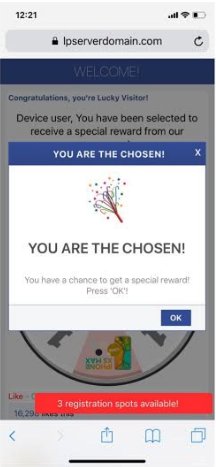
Assessment: A number of new redirect campaigns entered the ecosystem last weekend, impacting over 16M impressions across the majority of Ad Lightning partners. One campaign resolving to the "numberonevpn" and other similar domains was traced back to a malicious app, Outlaw VPN, which should be blocked by all sites as an advertiser.
Additional Details: Unique signatures are up almost 10% this week compared to the week prior, reflecting the increase in malicious activity.