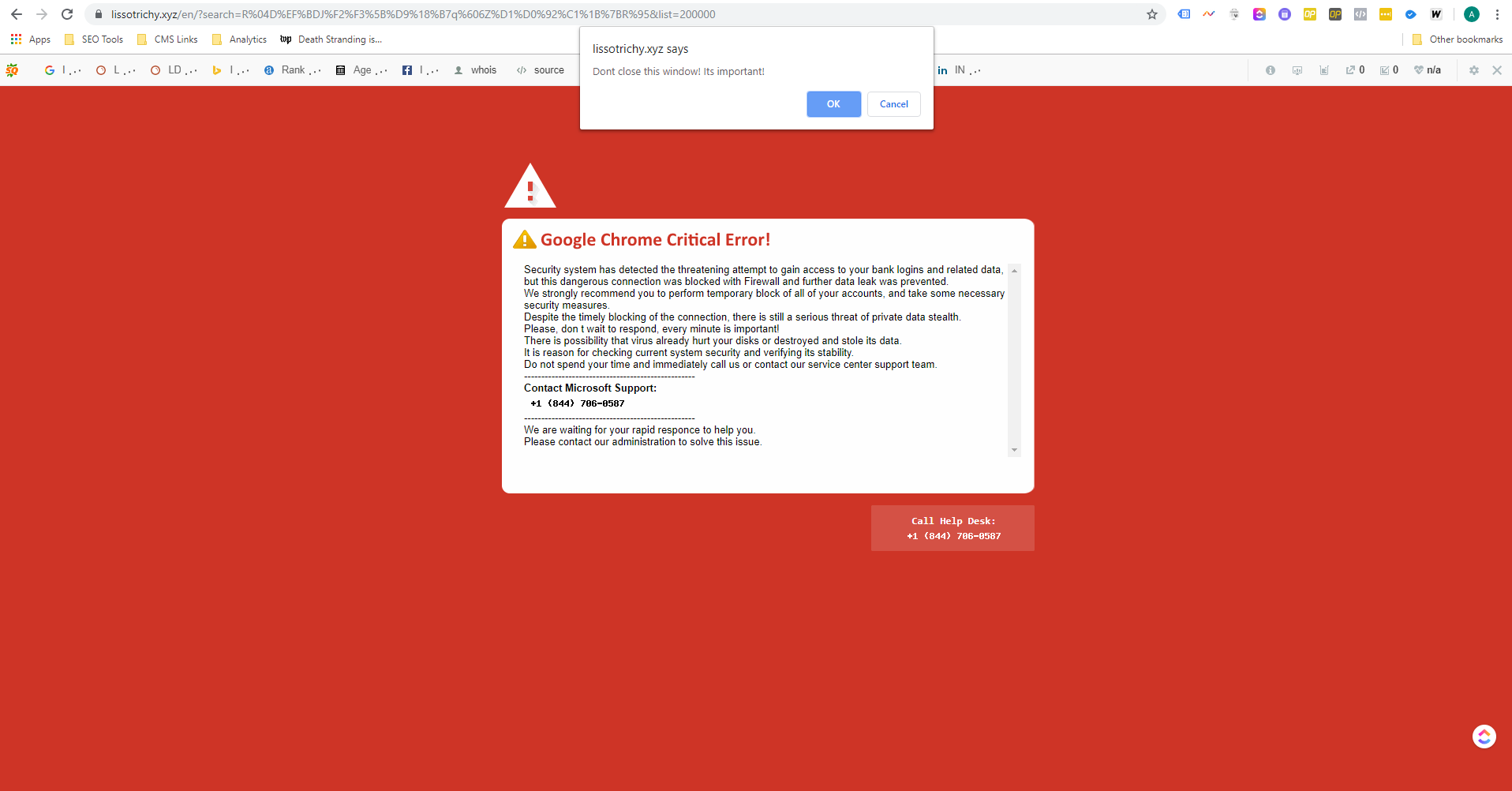
Assessment: November was an interesting month for malicious activity. Redirect campaigns spiked early in the month between 11/8 and 11/15. During that time, we noted an 800% increase in malicious ads in the system. The second spike in redirect activity occurred just prior to the Thanksgiving Holiday. Over 7M bad ads were detected and blocked in the days leading up to the long weekend.
One of the most commonly hijacked creatives this month was creative featuring Purdue University Global.

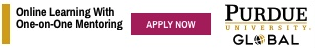
Fraudsters continue to use a common tactic of rotating malicious content between a variety of cloudfront endpoints to extend the life of the campaign and avoid detection. The malicious ads use various methods, like disabling “unsaved handlers”, to attempt a variety of redirect methods to expose holes in browser sandboxing, making the use of a blacklist critical to stop the behavior. In many cases, the ad tries to redirect right away, but if it fails, it then creates an input to look for user keyboard actions. When that is detected, it reacts to it with a redirection.
Sample redirect path:
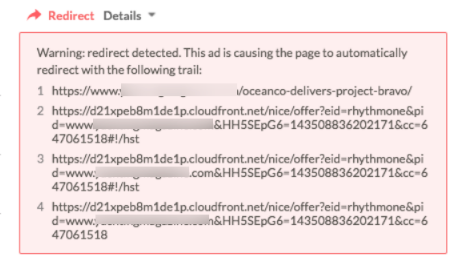
In terms of the content of the redirect, there's been a significant shift (nearly 200%) in redirects pointing to support scams versus "you've won" creative. These fraudsters are prompting users to call a number or click for support, either installing malware or looking to charge money.