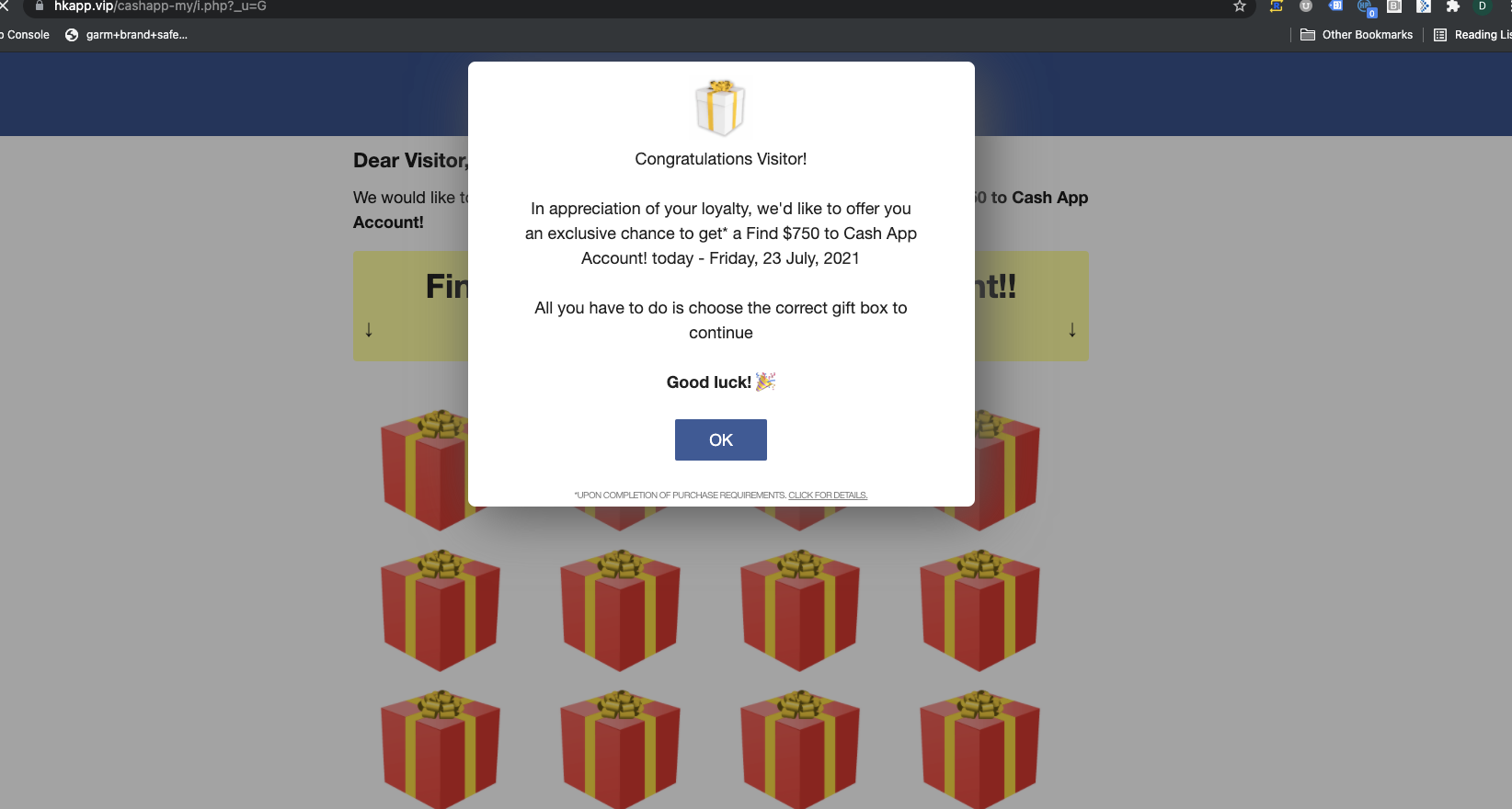
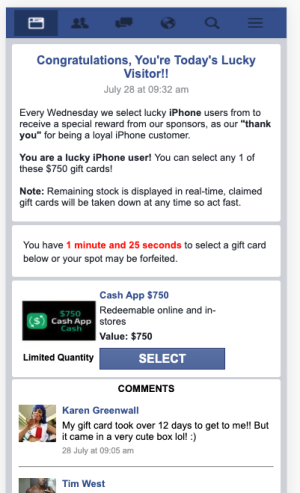
Assessment:
This malicious campaign has two methods of triggering the redirect. They attempt to load a script by writing a script call to a jquery file from http://ajax.googleapis.com and then run a function to replace all parts of the url to build the malicious payload and sends along fingerprinting information (screen w/h, platform, UA, color depth, number of plugins, timestamp, etc). It additionally loads a hidden iframe with a source that executes javascript that attempts to do a top.location.replace.
The ad that is loaded along with this malicious payload is a simple image (either a logo or a stolen Amazon Fire TV Stick ad) that actually takes a user to an Amazon listing for a firetv stick.
There seem to be two different campaigns active at the moment - one leading to healthnotetoday(dot)com and the other leading to various gift card scam pages.
Affected Platforms: GumGum (buyer has been blocked) & Between Digital