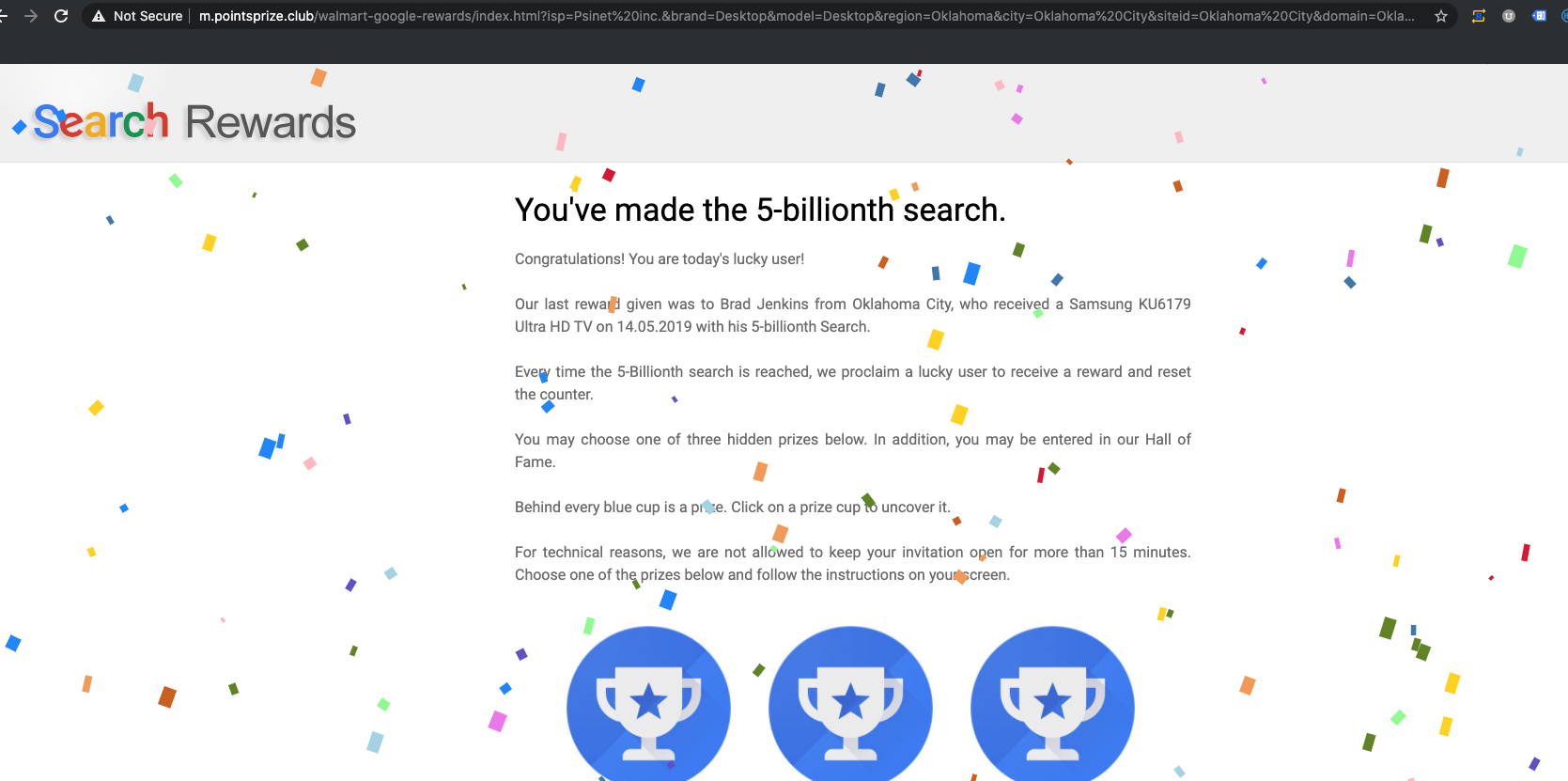
Assessment: Three separate redirect campaigns launched over the weekend.
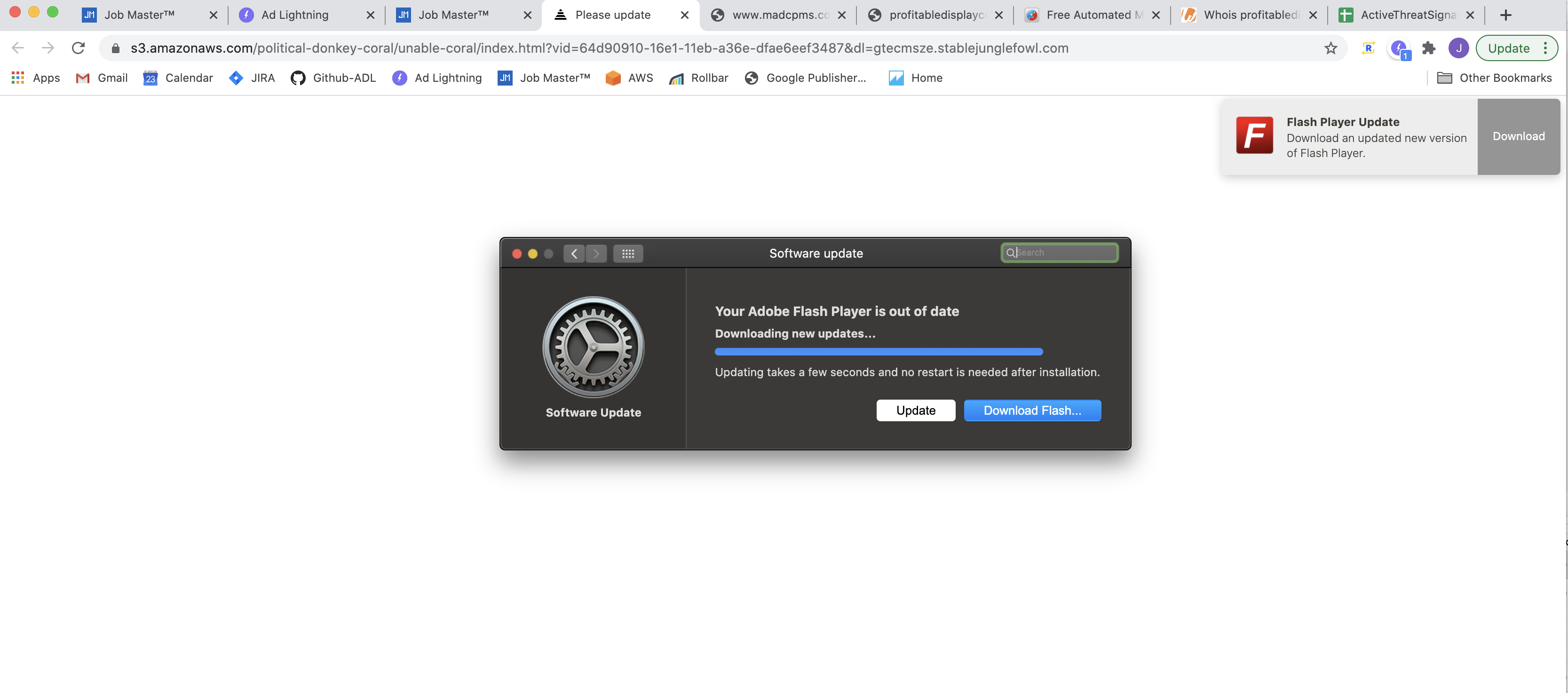
Threat #1: A script hosted on various raxcdn domains redirecting to domains such as licantrums[dot]com. Primarily impacted desktop users on Chrome and Safari.
Affected Platforms: Sovrn, Index & RhythmOne/Unruly

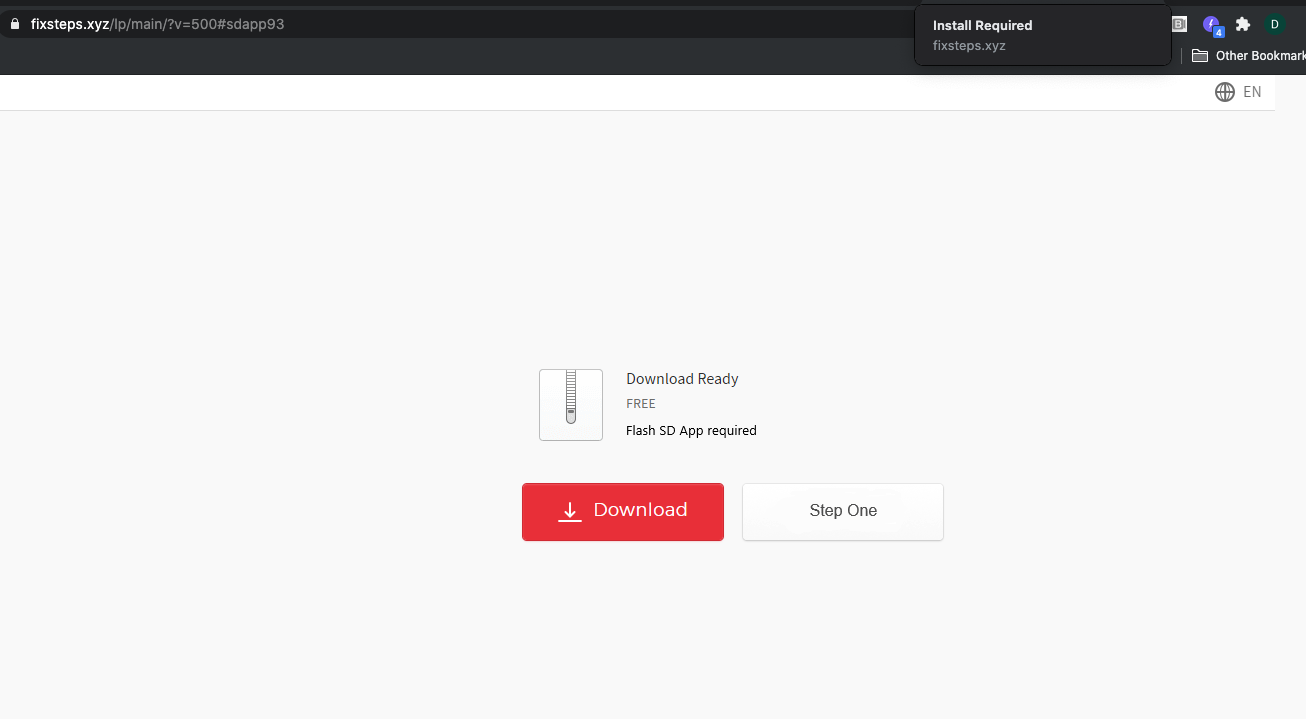
Threat #2: Campaign using steganography to forcefully redirect users to domains such as:
news12[dot]biz
lincolnnhattractions[dot]xyz
happyhattractions[dot]xyz
mediapicker[dot]com
performintenselyfreeapplication[dot]icu
performfreeintenselyapplication.icu
boot-upfree-theextremelyfile[dot]best
+ more
Sample Creative:

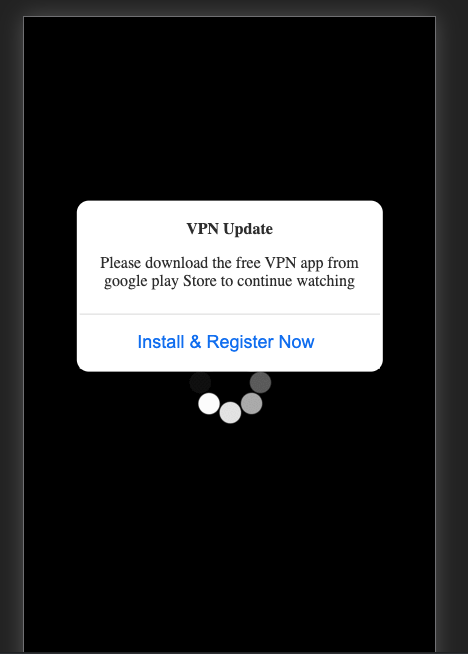
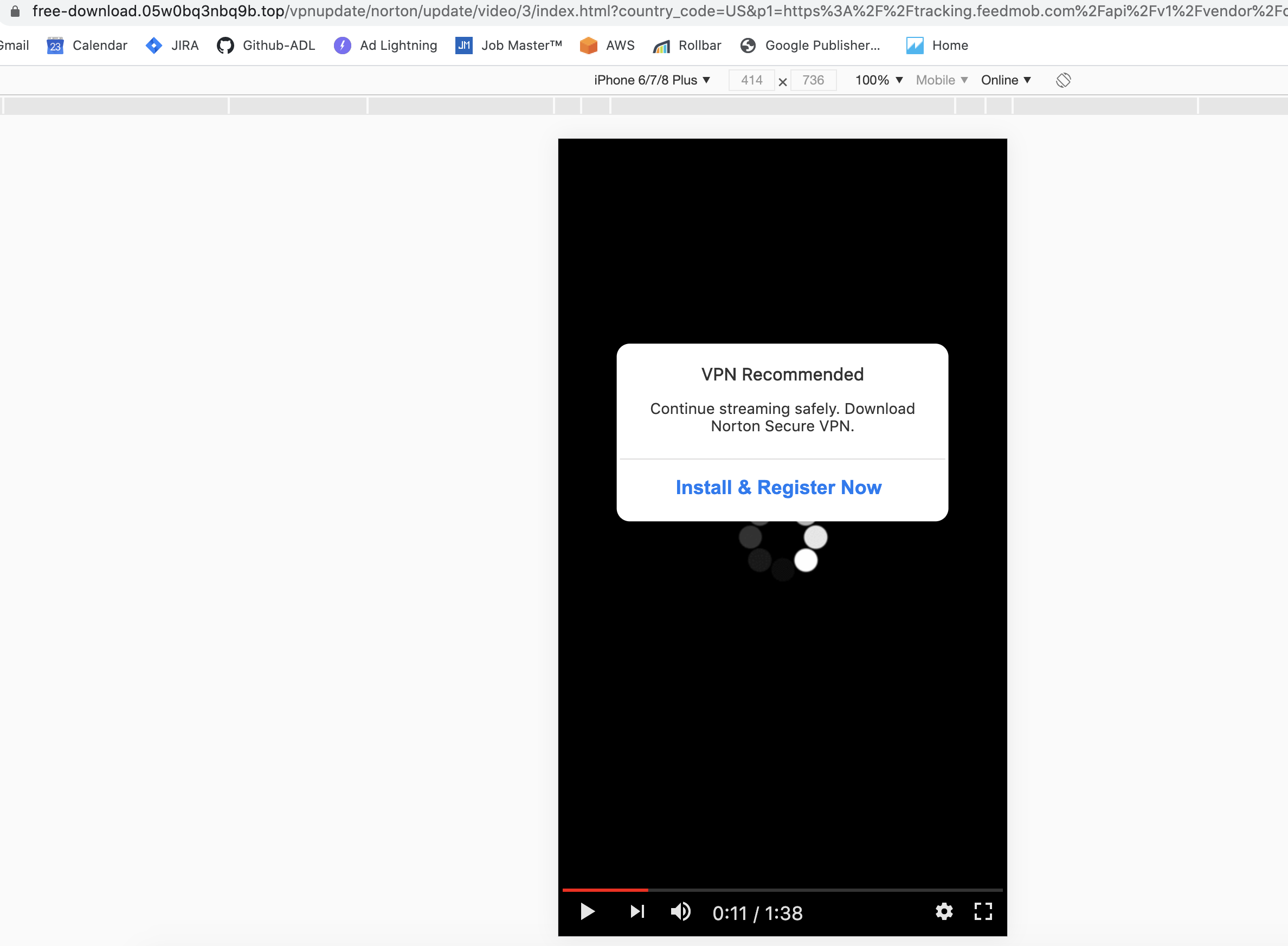
Threat #3: Campaign, primarily on desktop, driving users to a fake Norton Antivirus page.
Affected platforms: Bidmond DSP, Reklamstore DSP
Campaign Creative Examples: