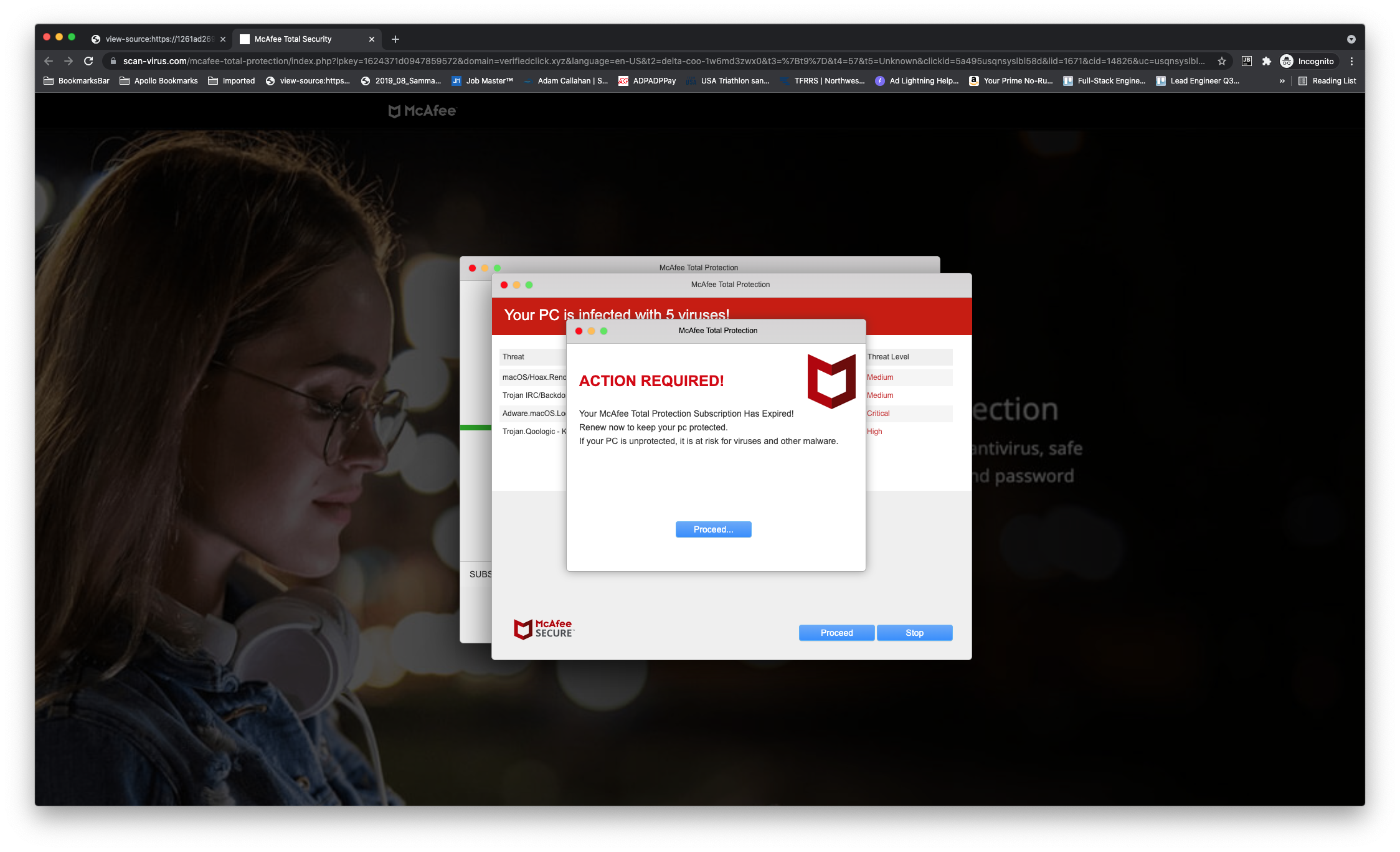
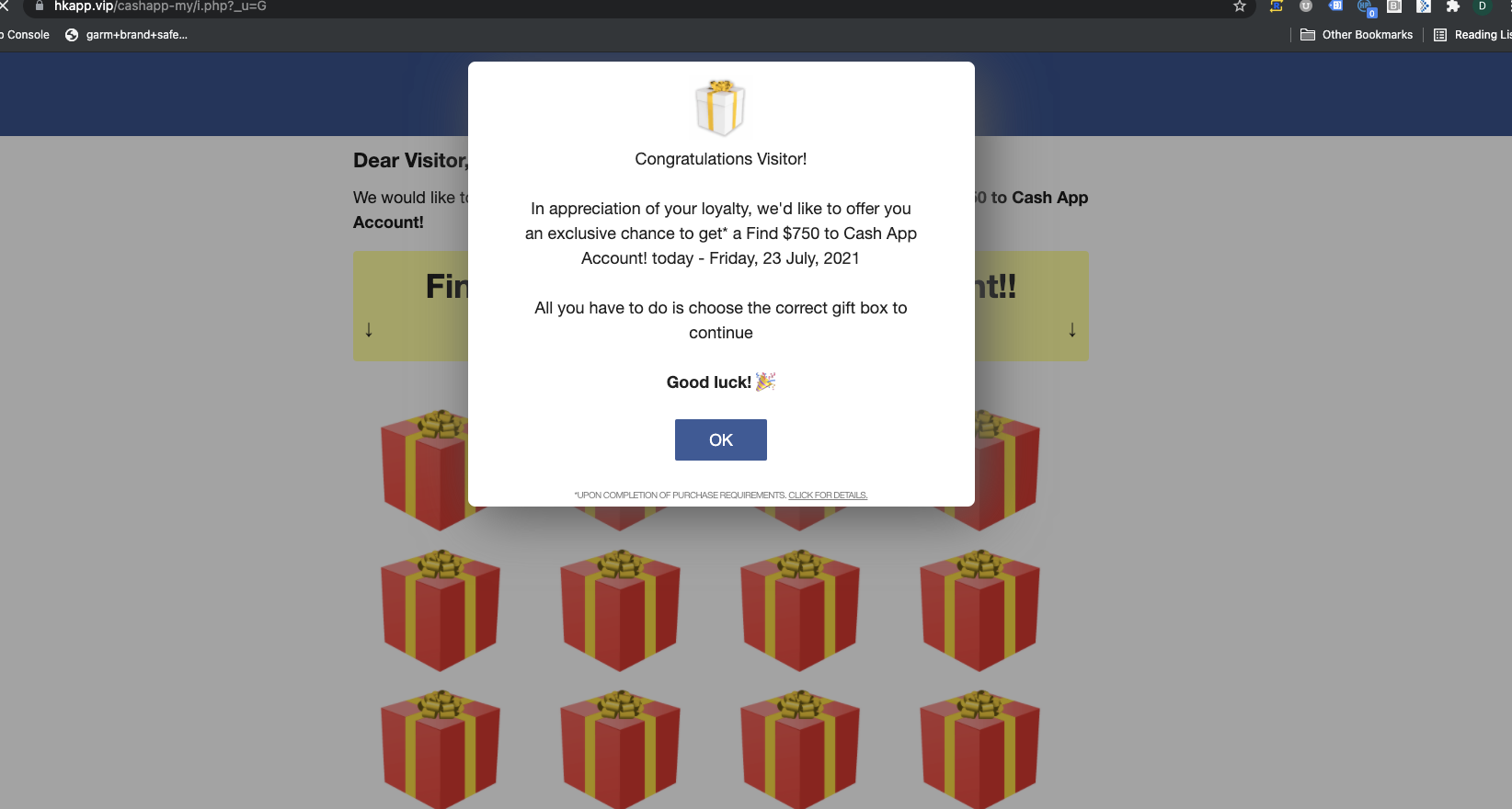
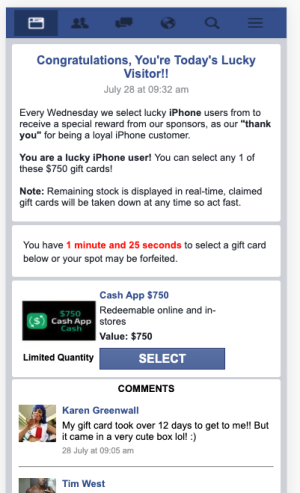
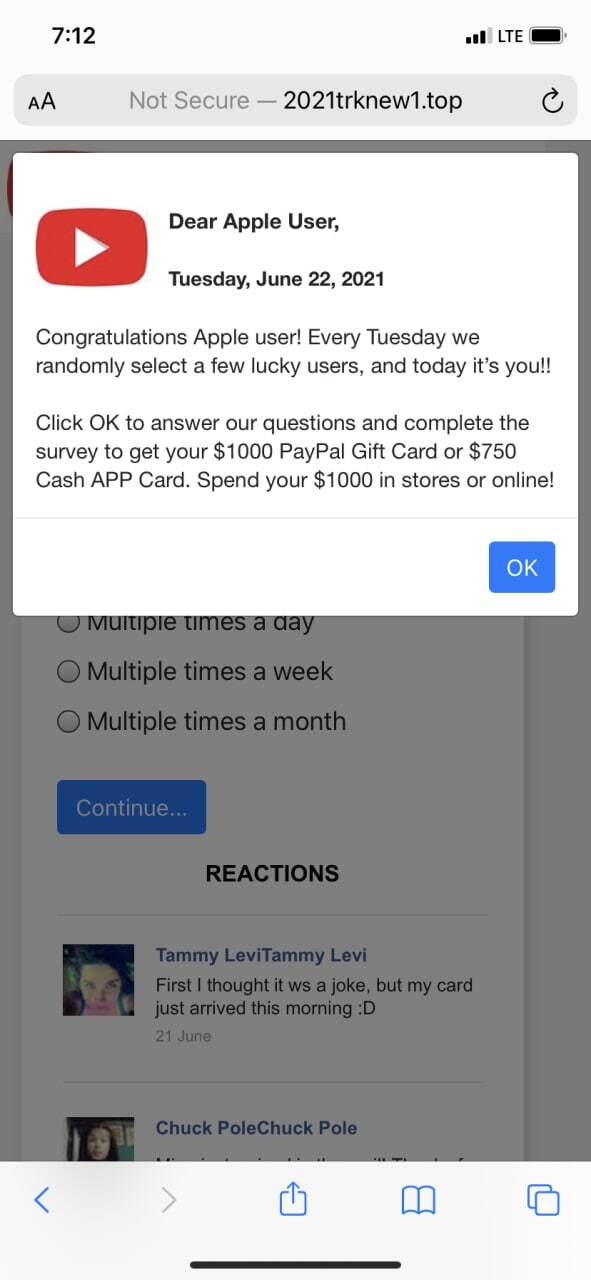
Assessment: Desktop redirect campaign impacting 1,300 domains. The malicious code itself relied on user inputs (such as click or scroll) to trigger the redirect. While this tactic is not new, it is a strategy that has been dormant for much of the year. Users were delivered a fake McAfee virus software popup prompting a download of more malicious code. The actual malicious ad code attempted to remove important functionality from the ad frame as well as the mainframe. This means that every time the redirection didn't occur there was also a risk that the page itself could break.
Interestingly, this campaign showed more sophistication in the code, collecting real-time data for analysis. Fraudsters added a random sampling of the ads, indicating that they expected large volumes of traffic, and planned to optimize their campaigns based on the learnings. The campaign, like many others, looked for the presence of blocking wrappers, in this case, ADL and two other competitors. This is something we expect, and have protection against, a nuance that all publishers/platforms should confirm with their providers.
Affected platforms: Early intelligence pointed to ReklamStore as the source of the redirects, however, ADL confirmed that Yieldmo was in fact the platform most impacted by this outbreak.